BLOG
Best Us Mobile Black-jack Software, Video game and you will Gambling enterprises 2024
Articles Simple tips to Gamble Online Blackjack Play Free and for Enjoyable Could you Earn At the Black-jack? Blackjack Online game Alternatives That is due primarily to the advantage on
NorgesAutomaten Remark ᐈ 100 Spins third Deposit Extra
NorgesAutomaten Remark ᐈ 100 Spins third Deposit Extra Posts All you need to find out about Norges Local casino an internet-based bettors Norges Gambling enterprise Liste More De Beste Bonustilbudene
Lowest Put Casinos
Blogs Tune in to Added bonus Small print At the step 1 Put Gambling enterprise Put step one And now have 50 Fs Betting Criteria To possess Platinum Play Local
Top ten Us Bitcoin Online casinos 2024
Blogs Slots Incentives And you may Promotions The five Finest Bitcoin Jackpot Ports So you can Choice The Btc For the Crypto Playing: The facts And just how Does it
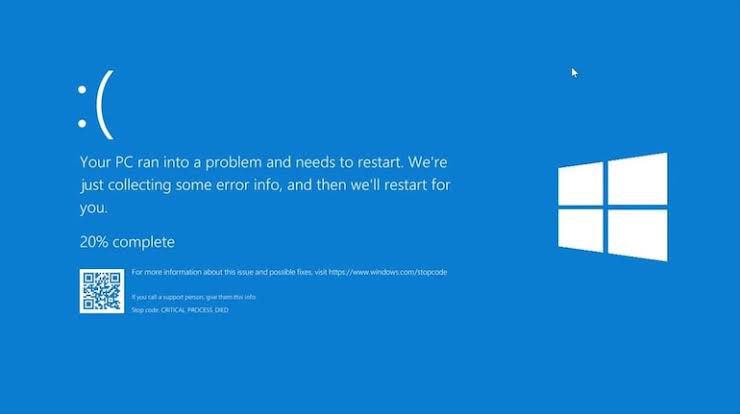
CrowdStrike Update Causes Widespread Blue Screen of Death on Microsoft Windows
A recent update from CrowdStrike, a prominent cybersecurity firm, has led to significant disruptions for Microsoft Windows users worldwide. The update has triggered the infamous Blue Screen of Death (BSOD),
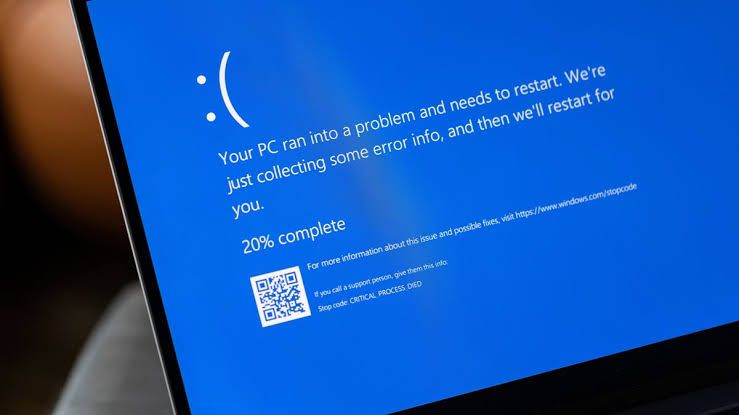
CrowdStrike Windows Outage: What Happened and What to Do Next
A recent update from CrowdStrike has caused significant disruptions for Windows users, leading to the notorious Blue Screen of Death (BSOD). This has primarily impacted organizations relying on CrowdStrike’s cybersecurity

Announcing Our Exciting Partnership with Gleac: Elevating Mentorship to New Heights!
We are thrilled to announce an exclusive partnership between Skillweed and Gleac, a cutting-edge mentorship platform that connects aspiring professionals with industry-leading mentors. This collaboration represents a significant milestone in

Exciting News: Skillweed Partners with CompTIA to Offer Industry-Leading Cybersecurity Certifications!
We are thrilled to announce a groundbreaking partnership between Skillweed and CompTIA, the largest body for cybersecurity certifications globally. This partnership marks a significant milestone for Skillweed and presents incredible

Malicious Npm Package “Oscompatible” Deploys Remote Access Trojan And Anydesk
Malicious Npm Package “Oscompatible” Deploys Remote Access Trojan And Anydesk A recent discovery has unveiled a malicious npm package, “oscompatible,” that is responsible for distributing a sophisticated remote access trojan

Zuckerberg’s Embrace of AI While Keeping the Metaverse Dream Alive
Zuckerberg’s Embrace of AI While Keeping the Metaverse Dream Alive Amidst the ascendancy of AI in the tech world, Mark Zuckerberg has reiterated his commitment to the metaverse, even as

Outsmarting Ransomware’s Evolving Tactics in 2024
Outsmarting Ransomware’s Evolving Tactics in 2024 The cybersecurity landscape of 2024 presents an ever-evolving challenge for professionals, especially in the relentless battle against ransomware. As these emerging threats continue to

Exploring the World of TikTok Shopping and Safeguarding Your Purchases
Exploring the World of TikTok Shopping and Safeguarding Your Purchases Recent research has shed light on a concerning trend: U.S. adults have collectively spent a staggering $71 billion on “impulse

Russian Hacker Group Coldriver Launches New Malware Campaign
Russian Hacker Group Coldriver Launches New Malware Campaign ColdRiver, a Russian hacker group notorious for its spear phishing tactics to acquire target credentials, has recently launched a fresh malware campaign,

Stable Code 3B: Transforming the Coding Landscape with AI
Stable Code 3B: Transforming the Coding Landscape with AI he arrival of AI in the world of software development represents a groundbreaking transformation, and the most recent advancement in this

Exploring the Marvels of Mobile AI with the Samsung Galaxy S24 Series
Exploring the Marvels of Mobile AI with the Samsung Galaxy S24 Series At the recent Galaxy Unpacked event, Samsung took the stage to showcase an impressive array of new AI

Revolutionizing Personalization: OpenAI Unveils GPT Store for Custom AI Assistants
Revolutionizing Personalization: OpenAI Unveils GPT Store for Custom AI Assistants Introduction: In an era where personalization is key, OpenAI has taken a monumental leap forward with the launch of its GPT

Asset Tracking Technologies: Exploring RFID, IoT, and Asset Tracking Software for Enhanced Asset Management
Asset Tracking Technologies: Exploring RFID, IoT, and Asset Tracking Software for Enhanced Asset Management Effective asset management is essential for businesses and organizations to optimize resources, reduce costs, and ensure

IT Asset Inventory: Importance and Best Practices for Comprehensive Asset Management
IT Asset Inventory: Importance and Best Practices for Comprehensive Asset Management In today’s digital age, IT assets are the backbone of every organization. From computers and servers to software licenses

Mastering LinkedIn’s Job Search: A Step-by-Step Guide
Mastering LinkedIn’s Job Search: A Step-by-Step Guide LinkedIn has evolved into more than just a professional networking platform; it is now a robust job search tool that connects job seekers

How to Showcase Your Certifications on Your LinkedIn Profile
How to Showcase Your Certifications on Your LinkedIn Profile LinkedIn has become an essential platform for professionals to network, build their personal brand, and showcase their skills and accomplishments. One

The Power of Personal Branding: Building Your LinkedIn Identity
The Power of Personal Branding: Building Your LinkedIn Identity In today’s competitive professional landscape, personal branding has emerged as a crucial element for career success. As the world’s largest professional

Securing The Mobile Workplace: Best Practices For Byod Cybersecurity
Securing The Mobile Workplace: Best Practices For Byod Cybersecurity As more companies embrace the flexibility and productivity benefits of the Bring Your Own Device (BYOD) trend, ensuring the security of

BYOD Policies: Strengthening Cybersecurity in the Bring Your Own Device Era
BYOD Policies: Strengthening Cybersecurity in the Bring Your Own Device Era As the Bring Your Own Device (BYOD) trend continues to gain momentum, organizations are faced with the challenge of

Demystifying the Orange Book: A Comprehensive Guide to Cybersecurity Standards
Demystifying the Orange Book: A Comprehensive Guide to Cybersecurity Standards In the realm of cybersecurity, standards play a crucial role in establishing guidelines and best practices for protecting sensitive information

Eavesdropping: Understanding the Risks and Protecting Your Privacy
Eavesdropping: Understanding the Risks and Protecting Your Privacy In an increasingly connected world, where communication takes place over various digital channels, the risk of eavesdropping has become a pressing concern.

Unveiling the CIA Triad in Cybersecurity: Confidentiality, Integrity, and Availability
Unveiling the CIA Triad in Cybersecurity: Confidentiality, Integrity, and Availability When it comes to cybersecurity, protecting sensitive information and ensuring the smooth operation of systems is paramount. To achieve these

Understanding Attack Vectors: Unveiling the Pathways to Cyber Threats
Understanding Attack Vectors: Unveiling the Pathways to Cyber Threats In the world of cybersecurity, attackers are constantly seeking vulnerabilities and weaknesses in systems to exploit. To better defend against such

Beyond Due Diligence: Advanced Best Practices In Third-Party Risk Management
Beyond Due Diligence: Advanced Best Practices In Third-Party Risk Management In an interconnected global business landscape, third-party partnerships have become an integral part of organizations’ operations. While these collaborations offer

Responsible Partnerships: Ethical Best Practices In Third-Party Risk Management
Responsible Partnerships: Ethical Best Practices In Third-Party Risk Management In an interconnected global business landscape, third-party partnerships have become an integral part of organizations’ operations. While these collaborations offer numerous

Building Resilience: Business Continuity And Disaster Recovery In Third-Party Risk Management
Building Resilience: Business Continuity And Disaster Recovery In Third-Party Risk Management In today’s interconnected business landscape, organizations heavily rely on third-party vendors, suppliers, and partners to achieve operational efficiency and

Safeguarding Your Digital Footprint: Best Practices For Data Privacy
Safeguarding Your Digital Footprint: Best Practices For Data Privacy In an increasingly digital world, our personal information is constantly being collected, stored, and shared. This raises concerns about data privacy

The Importance of Data Privacy: Protecting Your Personal Information
The Importance of Data Privacy: Protecting Your Personal Information In the age of digital connectivity, our personal information is constantly being collected, shared, and stored by various entities. While this

Introduction to Third-Party Risk Management: Understanding the Importance and Key Concepts
Introduction to Third-Party Risk Management: Understanding the Importance and Key Concepts In today’s interconnected business landscape, organizations are increasingly relying on third-party vendors, suppliers, and service providers to meet their

Developing an Effective Third-Party Risk Management Framework
Developing an Effective Third-Party Risk Management Framework In today’s interconnected business environment, organizations increasingly rely on external parties to fulfill critical functions. However, this reliance introduces risks that must be

The Human Factor: People-Centric Best Practices in Third-Party Risk Management
The Human Factor: People-Centric Best Practices in Third-Party Risk Management While technology and processes play a crucial role in Third-Party Risk Management (TPRM), it’s important not to overlook the human

Staying Ahead of the Curve: Emerging Best Practices in Third-Party Risk Management
Staying Ahead of the Curve: Emerging Best Practices in Third-Party Risk Management As the business landscape evolves, so do the risks associated with engaging third-party vendors, suppliers, and service providers.

The Role of Due Diligence in Third-Party Risk Management
The Role of Due Diligence in Third-Party Risk Management In today’s interconnected business landscape, organizations increasingly rely on third-party vendors, suppliers, and service providers to support their operations. However, with

Emerging Trends and Technologies in Third-Party Risk Management
Emerging Trends and Technologies in Third-Party Risk Management Third-party risk management has become increasingly complex due to the interconnected nature of today’s business landscape. As organizations continue to rely on

Best Practices for Continuous Monitoring Of Third-Party Risks
Best Practices for Continuous Monitoring Of Third-Party Risks In today’s interconnected business landscape, organizations often rely on third-party vendors, suppliers, and service providers to support their operations. While these partnerships

Best Practice To Handle Job Rejects And Keep Motivation
Best Practice To Handle Job Rejects And Keep Motivation Receiving a job rejection can be disheartening and may temporarily dampen your motivation. However, it is important to remember that job

Best Practice To Grow As A Leader Within An Organization
Best Practice To Grow As A Leader Within An Organization Growing as a leader within an organization requires continuous learning, self-reflection, and intentional actions. Here are some best practices to

Best Practice For Applying For A Job In Cyber Security
Best Practice For Applying For A Job In Cyber Security When applying for a job in cybersecurity, there are several best practices you can follow to increase your chances of

Cyber Threats | Skillweed
UNMASKING THE SHADOWS: EXPLORING THE EVOLVING LANDSCAPE OF CYBER THREATS The digital age has brought unprecedented connectivity and countless opportunities for innovation, but it has also given rise to a

Protect Online Data: Innovative Ways
INNOVATIVE APPROACHES TO SAFEGUARDING DIGITAL ASSETS In an era of sophisticated cyber threats and rapidly evolving digital landscapes, relying solely on traditional firewalls for safeguarding digital assets is no longer

Geomatics: Cybersecurity Key Controls
FIVE CYBERSECURITY KEY CONTROLS IN GEOMATICS Geomatics is a field that involves the collection, analysis, and interpretation of geographic data. Like all industries, Geomatics is vulnerable to cybersecurity threats, and

Five Top Threats in Critical Infrastructure
Critical infrastructure refers to the essential systems and services that are necessary for the functioning of modern society, including transportation, energy, water, telecommunications, and healthcare. Here are five top threats

All About Penetration Testing As A Service (PTAAS)
All About Penetration Testing As A Service (PTAAS) Penetration Testing as a Service (PTaaS) is a type of cybersecurity service that allows businesses and organizations to conduct regular penetration testing

IT Certifications 2023 | Skillweed
Most Lucrative and in Demand IT Certifications in 2023 Cybersecurity is growing day by day. As technology keeps on developing, cybersecurity and any other IT area will keep on growing

Selling PC Tips | Skillweed
ESSENTIAL THINGS TO DO BEFORE YOU SELL YOUR OLD COMPUTER FOR CYBERSECURITY PURPOSES This is one of the ways for you to make some cash from the sale of your

Essential Cybersecurity Tips & Controls
Essential Cybersecurity Controls There are many different cybersecurity controls that organizations can implement to protect their systems and data, but here are some of the essential ones: Access controls Access

Top AI in Cybersecurity | Skillweed
Top Five Application of AI in Cybersecurity Threat detection is one of the primary applications of AI in cybersecurity, and it involves using machine learning algorithms to identify and respond

OpenAI Guide | Skillweed
ALL ABOUT OPENAI PLAYGROUND OpenAI’s latest product, ChatGPT has gone viral. Everyone is talking about it. Now the world is starting to change through artificial intelligence. OpenAI is at the

Top AI Platforms: Transforming Industries
PLATFORMS TAKING AI TRANSFORMATION TO A NEW LEVEL AI is transforming the internet world, and we are enjoying! Now everyone is talking about ChatGPT, an AI chatbot that gives all

Understanding Open AI Technology
WHAT IS OPENAI SINCE EVERYBODY IS TALKING ABOUT CHATGPT Everyone is talking about ChatGPT. Of course, it is the best technological innovation we have witnessed in 2022, which is going

What is ChatGPT? | Skillweed
ALL ABOUT CHATGPT – AN AI CHATBOT Introduction Everyone is talking about ChatGPT. Some say it is a robot, while others say it is an alien application. But the truth

Importance of User Data | Skillweed
WHY DATA IS NEW OIL Introduction The oil refinery has been the symbol of extraction and refining of power for decades now. Oil has been, for decades, a source of

Leverage Data Intelligence: Enhance Life
INTELLIGENCE DATA, A WAY OF LIFE The use of intelligence data is growing among governments and organizations. The data is used to help make decisions on various issues, including national

Data Science: A Top-Paying IT Job
WHY IS DATA SCIENCE A TOP-PAYING CAREER? Data science is a relatively new field that is rapidly growing in popularity. Due to the high demand for data science skills, data

Cybersecurity Certifications 2 | Skillweed
TOP 3 CYBER THREATS SEPTEMBER 2022 This year, especially on the month of September, a lot has happened in cybersecurity world. The year is almost ending, however we have witnessed

Excel Efficiency | Skillweed
WAYS TO BE EFFICIENT IN EXCEL Excel is a powerful program that can be of great advantage if you can master some of its hidden secrets. There are many great